
General Data Protection Regulation
The regulation applies if the data controller (an organisation that collects data from EU residents), or processor (an organisation that processes data on behalf of a data controller like cloud service providers), or the data subject (person) is based in the EU. Under certain circumstances,[7] the regulation also applies to organisations based outside the EU if they collect or process personal data of individuals located inside the EU. The regulation does not apply to the processing of data by a person for a “purely personal or household activity and thus with no connection to a professional or commercial activity.”
Personal data is any information relating to an individual, whether it relates to his or her private, professional or public life. It can be anything from a name, a home address, a photo, an email address, bank details, posts on social networking websites, medical information, or a computer’s IP address.”[8]
Most Important IT Implementation:
Art.15 – Right of access by the data subject
Information regarding recipients and storage time of personal data.
IT implementation
Rights management for shared content; auditing / logging
Art.17 – Right to erasure (‘right to be forgotten’)
Obligation to delete personal data immediately upon request.
IT implementation
Full data control through on-premises storage; file versioning;
trash bin with final file deletion; expiration date for shares and shares.
Art.20 – Right to data portability
On request, personal data must be transmitted in a structured, common and machine-readable format.
IT implementation
All user data must be fully logged and exportable.
Art.24 – Responsibility of the controller
The controller responsible for processing must ensure and provide proof that processing is carried out in accordance with the regulations.
IT implementation
Auditing / logging ; full transparency and system control
Art.25 – Data protection by design and by default
The data protection principles and the necessary processing safeguards shall be effectively implemented by the controller.
IT implementation
Product design – security and privacy by default with full control function.
Art.32 – Security of processing
Those responsible and contract processors shall take appropriate technical and organizational measures to ensure a level of protection commensurate with the risk.
IT implementation
Multi-factor authentication; client-side end-to-end encryption; file firewall; Ransomware Protection; rights management; auditing/logging; password policies; file integrity check.
Art.34 – Communication of a personal data breach
Notification obligation is not required if, for example, security measures such as encryption are in place.
IT implementation
Client-side end-to-end encryption; server-side encryption
The EU General Data Protection Regulation (GDPR) delivers a fundamental change in how data controllers and data processors handle personal data. Instead of an ‘add-on’ or
afterthought within business operations, protections for personal data will now have to be designed by DEFAULT into the very fabric of data processing systems, meaning that entities will need to re-examine how they approach the use of technology in their organisations
Simple approach:
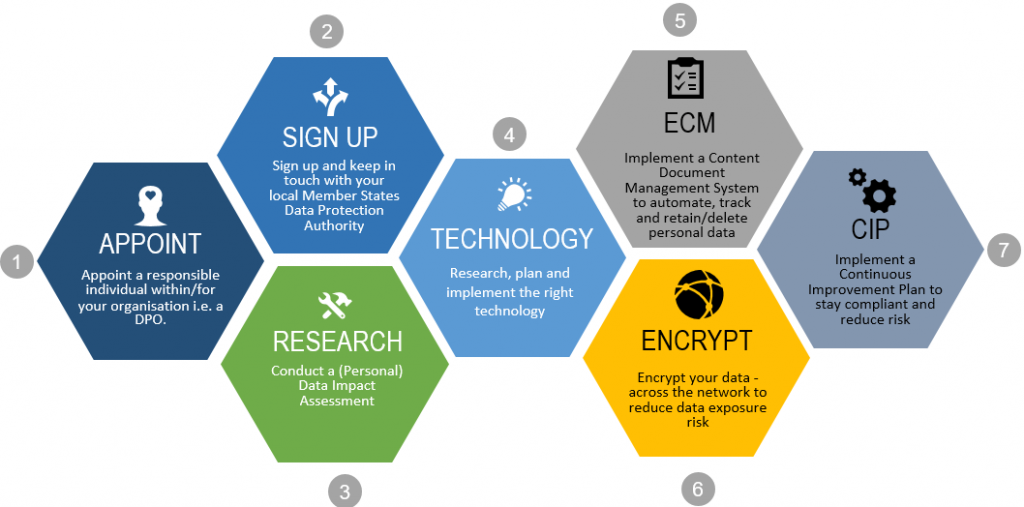
IBM approach:

GPDR Coalition:

GLOSSARY
Data controller (organisation) means “the natural or legal person, public authority, agency or other body which, alone or jointly with others, determines the purposes and means of the processing of personal data”.
Data subject (individual) means an identifiable natural person “who can be identified, directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, or an online identifier.
Personal data means “any information relating to an identified or identifiable
natural person (‘data subject’)”. The Regulation states this also includes online
identifiers such as IP addresses and cookies.
Data processor (service providers) means “a person, public authority, agency
or other body which processes personal data on behalf of the controller”. An example is a
Cloud provider that offers data storage.
references:
EU_GDPR
technologys-role-in-data-protection-the-missing-link-in-gdpr-transformation
ibm-security-solutions-wg-white-paper-external
Wiki]]>
